Email Security Basics
As the Head of ICT for a large (by NZ Standards) company that does business in 84 different countries our company does a lot of communications with our customers via electronic means.
On an almost daily basis, I’m surprised at the number of companies that don’t employ the very basic protocols DMARC, DKIM and SPF to protect their organisation from nefarious parties trying to impersonate them, perhaps because they are technically based (and poorly named) and on the whole not well understood as they rely on the SENDING organisation to set them up.
So what is DMARC, DKIM and SPF?
These are text records that are added to your domain (e.g., @example.com) that allows the receiver to check that the message sent came from your organisation. By adding these records if other people try to send mail claiming to be from your organisation then most modern mail filtering platforms have the ability to see the red flag and know something isn’t right and quarantine the message for someone to check.
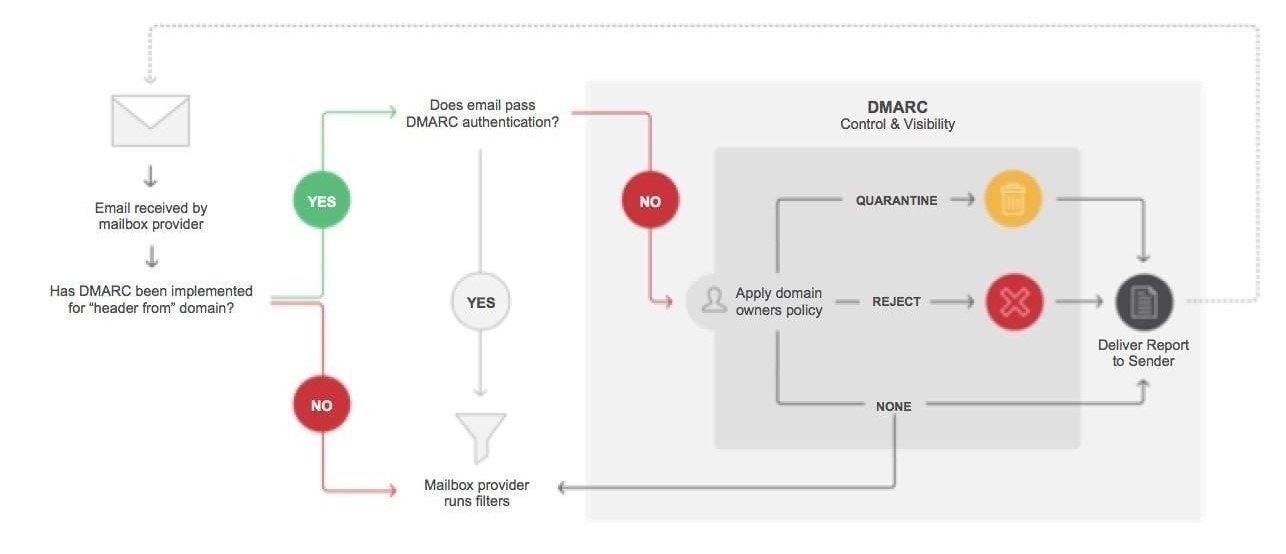
DMARC
DMARC is simply an aggregator service to determine whether the sender uses SPF and DKIM, and how the sender recommends receivers should treat failed/spoofed emails claiming to be from the sender’s domain. Essentially it’s how you tell the world what to do and whom to contact when someone tries to impersonate your company
DKIM
DKIM works by preventing the spoofing of the “Display From” email address shown to an end-user when they preview or open an email. Hackers use this to send from a random address but make mail seem as if it’s come from a legitimate source.
SPF
SPF works by preventing spoofing of a legitimate email real return address (i.e., the email address that you would be sending a reply to) domain. Hackers use this to get mail back to their random address rather than have it go back to the sender they are impersonating
WARNING
SPF, DKIM DMARC will not stop all malicious email, for many reasons including these:
The hacker could be sending a malicious email from within a compromised domain environment (they have already hacked the sender and are legitimately sending as them)
The hacker could be using a domain that enables and uses SPF and DKIM
Legitimate email sometimes fails these protocols
As such they should be treated as the red flags they are for quarantining mail to ensure it definitely came from where it says it came from.
So how can you help?
Talk to your IT team or your IT provider about getting these protocols setup for your domain. This will help protect your organisation’s brand and image, and it will protect your customers and partners from attack by allowing their security tools to appropriately quarantine mail that may seem like it came from your organisation.